CERT-In (Indian Computer Emergency Response Team), din cadrul MeitY (Ministerul Electronicii și Tehnologiei Informației), și-a extins în mod constant rolul de autoritate națională pentru securitatea cibernetică de la desemnarea sa în temeiul Legii de modificare a tehnologiei informației din 2008.
În 2024, CERT-In a emis primele sale orientări dedicate SBOMSoftware Bill of Materials), definind elementele minime, formatele și cerințele de implementare.
Doar un an mai târziu, în iulie 2025, versiunea 2.0 a extins semnificativ domeniul de aplicare, extinzând acoperirea la SBOM, QBOM, CBOM, AIBOM și HBOM, stabilind în continuare lanțurile sigure de aprovizionare cu software ca o strategie națională de rezistență de bază.
Pentru CIO și CISO, aceste orientări au consecințe operaționale, financiare și de reglementare. Organizațiile trebuie să fie pregătite să demonstreze practici SBOM pregătite pentru audit, să alinieze furnizorii și partenerii la cerințele de conformitate și să adopte automatizarea pentru a gestiona SBOM la scară largă.
Acest articol oferă o foaie de parcurs pas cu pas pentru a obține conformitatea cu liniile directoare CERT-In SBOM, acoperind domeniul de aplicare, standardele tehnice, selectarea furnizorilor și cele mai bune practici pentru întreprinderile indiene și organizațiile globale cu operațiuni în India.
- Orientările CERT-In SBOM: Domeniu de aplicare, aplicabilitate și cerințe cheie
- Cum ajută OPSWAT SBOM la îndeplinirea cerințelor CERT-In
- Alinierea componentelor Software cu conformitatea CERT-In SBOM
- Formate SBOM acceptate și standarde tehnice în cadrul CERT-In
- Cum să evaluați și să selectați furnizorii de conformitate SBOM
- Cele mai bune practici pentru implementarea SBOM fără întreruperi
- Automatizare, conformare și protecție: Abordarea OPSWAT pentru gestionarea SBOM
- Lanțul de aprovizionare cuSoftware MetaDefender
- Întrebări frecvente
- Considerații specifice sectorului: Instituții financiare, Supply Chain și infrastructura critică
- Ce urmează? Pregătirea pentru Cert-In SBOM Guidelines este esențială
Orientările CERT-In SBOM: Domeniu de aplicare, aplicabilitate și cerințe cheie
Ce este CERT-In și de ce a emis orientări SBOM?
CERT-In este agenția națională de securitate cibernetică din India. Orientările sale SBOM vizează consolidarea securității lanțului de aprovizionare, îmbunătățirea vizibilității componentelor software și asigurarea unor răspunsuri mai rapide și standardizate la vulnerabilități.
Ce este CERT-In și de ce a emis orientări SBOM?
Conformitatea se aplică guvernului, sectorului public, serviciilor esențiale și exportatorilor de software, precum și dezvoltatorilor, integratorilor și revânzătorilor de-a lungul întregului ciclu de viață al software-ului.
Elementele Core ale unui SBOM conform orientărilor CERT-In
În conformitate cu orientările, SBOM trebuie să includă date precum:
- Numele componentei, versiunea, furnizorul și licența
- Dependențe și origine
- Vulnerabilități și starea patch-urilor
- Date de expirare a duratei de viață, restricții de utilizare și criticitate
- Identificatori unici, sume de control și informații despre autor
Cerând aceste elemente minime, CERT-In se asigură că SBOM-urile sunt acționabile, lizibile automat și pregătite pentru audit.
Cum ajută OPSWAT SBOM la îndeplinirea cerințelor CERT-In
OPSWAT SBOM ajută la automatizarea și colectarea câmpurilor de date CERT-In SBOM, pentru a oferi vizibilitate și transparență în principalele domenii, de la detalii privind componentele software, transparență și riscuri, până la licențe și utilizare.
Detalii privind componenta Software
- Numele componentei: Numele componentei software sau al bibliotecii.
- Versiunea componentei: Numărul versiunii sau identificatorul componentei.
- Furnizor de componente: Entitatea care furnizează componenta (furnizor, terță parte sau open-source).
- Originea componentei: Sursa componentei (proprietară, open-source sau terță parte).
- Identificator unic: Cod distinct pentru urmărirea componentei de-a lungul versiunilor și proprietății.
- Autorul datelor SBOM: Entitatea responsabilă de crearea înregistrării SBOM.
- Timestamp: Data și ora la care a fost înregistrată intrarea SBOM.
Transparența și riscurile Software
- Dependențe de componente: Alte componente sau biblioteci pe care se bazează aceasta.
- Vulnerabilități: Probleme de securitate cunoscute legate de componentă, cu severitatea și referințele CVE.
- Starea patch-ului: Actualizarea curentă sau disponibilitatea patch-urilor pentru vulnerabilități.
- Checksum-uri sau Hash-uri: Valori criptografice pentru verificarea integrității fișierelor.
- Proprietate executabilă: Dacă componenta poate fi executată.
- Proprietate arhivă: Dacă componenta este împachetată ca un fișier arhivă.
- Data lansării: Data la care componenta a fost lansată pentru prima dată.
Licențiere și utilizare
- Licența componentei: Tipul de licență și termenii care reglementează utilizarea componentei.
- Restricții de utilizare: Limitări legale sau de reglementare privind utilizarea componentelor.
Alinierea componentelor Software cu conformitatea CERT-In SBOM
Atingerea conformității CERT-In este o călătorie în etape care necesită coordonarea între echipele de dezvoltare, securitate, operațiuni și conformitate. Fiecare parte interesată joacă un rol în crearea, menținerea și partajarea SBOM-urilor în diferite momente ale ciclului de viață al software-ului.
Tabelul de mai jos, care conține conținut și exemple din Orientările tehnice CERT-In, ilustrează modul în care responsabilitățile SBOM se aliniază cu componentele software comune:
| Software | Exemplu | Nivelul SBOM | SBOM Autor | De ce? |
|---|---|---|---|---|
| Aplicație principală | O aplicație de analiză a datelor | SBOM la nivel de aplicație | Creat de echipa de dezvoltare a produsului | SBOM complet livrat împreună cu aplicația către client sau autoritatea de reglementare |
| Componentă Software cheie [bază de date, cadru] | PostgreSQL | SBOM de nivel superior | Dezvoltat intern în cazul în care furnizorul nu a furnizat un SBOM | Asigură trasabilitatea componentelor critice |
| Platformă/Middleware [de exemplu, server web, mediu de execuție] | Server Apache Tomcat | Livrare SBOM | Furnizat de platformă/vendor | Partajat la achiziție; integrează componente furnizate de furnizor |
| Biblioteci terță parte/SDK-uri | Postfix & Twilio SDK | SBOM tranzitiv | Creat de furnizorul din amonte sau intern dacă nu este disponibil | Acoperă dependențele indirecte și serviciile externe |
Odată definite rolurile și responsabilitățile, organizațiile pot trece la etapele practice ale conformității. O foaie de parcurs etapizată contribuie la maturizarea oamenilor, proceselor și tehnologiei.
1. Efectuarea unei evaluări a pregătirii și a unei analize a lacunelor
Identificarea practicilor actuale pentru inventarul software, urmărirea vulnerabilităților și SBOM-urile furnizate de furnizori. Comparați aceste practici cu câmpurile și formatele de date cerute de CERT-In.
2. Crearea unei politici interne SBOM și a unei structuri de guvernanță
Definiți roluri clare pentru dezvoltatorii, operațiunile IT, echipele de achiziții, securitate și conformitate. Guvernanța asigură că SBOM-urile sunt create, menținute și partajate în mod consecvent în întreaga întreprindere.
3. Selectarea și implementarea instrumentelor de generare SBOM
Automatizarea este esențială. Instrumentele trebuie:
- Generați SBOM-uri pentru fiecare versiune, patch sau actualizare nouă
- Integrarea cu conductele DevOps, depozitele de surse și registrele de containere
- Ieșire în formate CycloneDX și SPDX pentru alinierea reglementărilor
4. Integrarea fluxurilor de lucru SBOM în SDLC și Achiziții
Integrați generarea SBOM în fiecare etapă SDLC:
- Proiectare SBOM: componente planificate
- SBOM sursă: dependențe de dezvoltare
- Build SBOM: în timpul compilării
- SBOM analizat: inspecție după construcție
- SBOM implementat: mediu instalat
- SBOM în timp real: monitorizarea componentelor active
Contractele de achiziții ar trebui să impună tuturor furnizorilor să furnizeze SBOM.
5. Menținerea permanentă a conformității și a pregătirii pentru audit
Stabiliți actualizări continue ale SBOM, integrați-le cu avize privind vulnerabilitățile, precum VEX (Vulnerability Exploitability eXchange) și CSAF, și asigurați stocarea și partajarea securizate prin criptare, HTTPS și semnături digitale.
Doriți să aflați cum să valorificați SBOM pentru strategia dumneavoastră de securitate?
Formate SBOM acceptate și standarde tehnice în cadrul CERT-In
CycloneDX și SPDX: Standardele acceptate
CERT-In recunoaște CycloneDX și SPDX ca formate principale care pot fi citite automat pentru automatizarea SBOM.
- CycloneDX: ușor, centrat pe securitate, optimizat pentru gestionarea vulnerabilităților
- SPDX: axat pe licență, adoptat pe scară largă pentru documentația de conformitate
Cum să evaluați și să selectați furnizorii sau soluțiile de conformitate CERT-In SBOM
Selectarea furnizorului sau a soluției potrivite este esențială atât pentru conformitate, cât și pentru eficiența operațională.
Criterii cheie pentru evaluarea furnizorilor de conformitate CERT-In SBOM
- Suport pentru SPDX și CycloneDX
- Integrarea cu conductele DevOps și fluxurile de lucru CI/CD
- Abilitatea de a genera mai multe niveluri SBOM (proiectare, construcție, implementare, timp de execuție)
- Rapoarte pregătite pentru audit și mecanisme sigure de partajare
Întrebări pe care trebuie să le adresați furnizorilor potențiali cu privire la alinierea CERT-In
Selectarea partenerilor potriviți este la fel de importantă ca și crearea proceselor SBOM interne. Directorii informatici și responsabilii cu achizițiile ar trebui să includă alinierea CERT-In în listele de verificare ale RFP-urilor și ale due diligence-ului. Întrebările cheie pe care trebuie să le puneți includ:
- Furnizați SBOM-uri în formate aprobate de CERT-In (SPDX, CycloneDX)?
- Cât de des sunt actualizate SBOM-urile dumneavoastră - numai la lansare sau în mod continuu?
- Ce automatizare oferiți pentru generarea, validarea și partajarea securizată a SBOM?
- Cum impuneți distribuirea securizată a SBOM (de exemplu, criptare, RBAC, semnături digitale)?
- Soluția dvs. se integrează cu conductele DevOps, bazele de date privind vulnerabilitățile și avizele CERT-In?
- Cum sprijiniți auditurile de conformitate și raportarea continuă de reglementare?
Punerea acestor întrebări în avans contribuie la asigurarea faptului că furnizorii nu sunt conformi doar pe hârtie, ci și capabili să susțină practicile SBOM care se aliniază la orientările în continuă evoluție ale CERT-In.
Lista de verificare pentru selectarea și integrarea furnizorilor
- Suportă câmpurile și formatele de date cerute de CERT-In
- Automatizează generarea, urmărirea și actualizările
- Oferă controale de acces bazate pe roluri și partajare securizată
- Adoptare demonstrată în industriile reglementate
Cele mai bune practici pentru implementarea SBOM fără întreruperi
Strategii dovedite pentru întreprinderile mari
- Începeți cu fluxurile de lucru de bază și extindeți maturitatea în timp
- Obligativitatea furnizării SBOM în toate contractele de achiziții publice
- Adoptarea unei abordări shift-left prin integrarea generării SBOM la începutul SDLC
- Formarea personalului privind conștientizarea SBOM și cerințele de reglementare
Greșeli frecvente și cum să le evitați
Chiar și inițiativele SBOM bine intenționate pot eșua dacă organizațiile le abordează cu superficialitate. CERT-In subliniază faptul că SBOM-urile trebuie să fie exacte, cuprinzătoare și actualizate continuu. Iată câteva dintre cele mai frecvente capcane și cum să le evitați:
| Greșeală frecventă | Explicație | Cum să o evitați |
|---|---|---|
| Tratarea SBOM ca un raport static | Multe organizații generează un SBOM la lansare și nu îl actualizează niciodată. Acest lucru le lasă nevăzute la vulnerabilitățile introduse de patch-uri, actualizări sau noi dependențe. | Tratați SBOM ca pe un inventar viu. Automatizați actualizările prin intermediul conductei CI/CD, astfel încât fiecare nouă construcție sau versiune să actualizeze datele SBOM. |
| Eșecul de a include dependențele transitive | Ignorarea componentelor indirecte, cum ar fi bibliotecile open-source introduse de alte dependențe, creează puncte moarte periculoase pe care atacatorii le exploatează. | Utilizați instrumente automate de generare SBOM care cartografiază recursiv toate dependențele directe și tranzitive, asigurând acoperirea completă a întregului lanț de aprovizionare software. |
| Bazarea pe crearea manuală fără automatizare | Compilarea manuală a SBOM este consumatoare de timp, predispusă la erori și nesustenabilă la nivel de întreprindere. De asemenea, crește riscul de formate inconsecvente. | Integrați automatizarea și standardizarea. Adoptați instrumente care generează SBOM-uri în formate aprobate de CERT-In, precum SPDX și CycloneDX, și impuneți validarea înainte de lansare. |
Prin evitarea acestor greșeli și integrarea practicilor SBOM în fluxurile de lucru zilnice de dezvoltare, organizațiile pot transforma conformitatea într-un avantaj strategic, reducând riscurile și îndeplinind în același timp cerințele CERT-In.
Pregătirea pentru audituri
Menținerea depozitelor SBOM complete, documentarea practicilor de guvernanță și alinierea la modelele de audit CERT-In.
Pregătirea pentru viitor împotriva schimbărilor de reglementare
Foaia de parcurs a CERT-In face deja aluzie la cerințe mai largi în materie de BOM (hardware, AI și cloud). Întreprinderile care adoptă instrumente scalabile și flexibile vor fi cel mai bine poziționate pentru a se adapta.
Automatizare, conformare și protecție: Abordarea OPSWAT pentru gestionarea SBOM
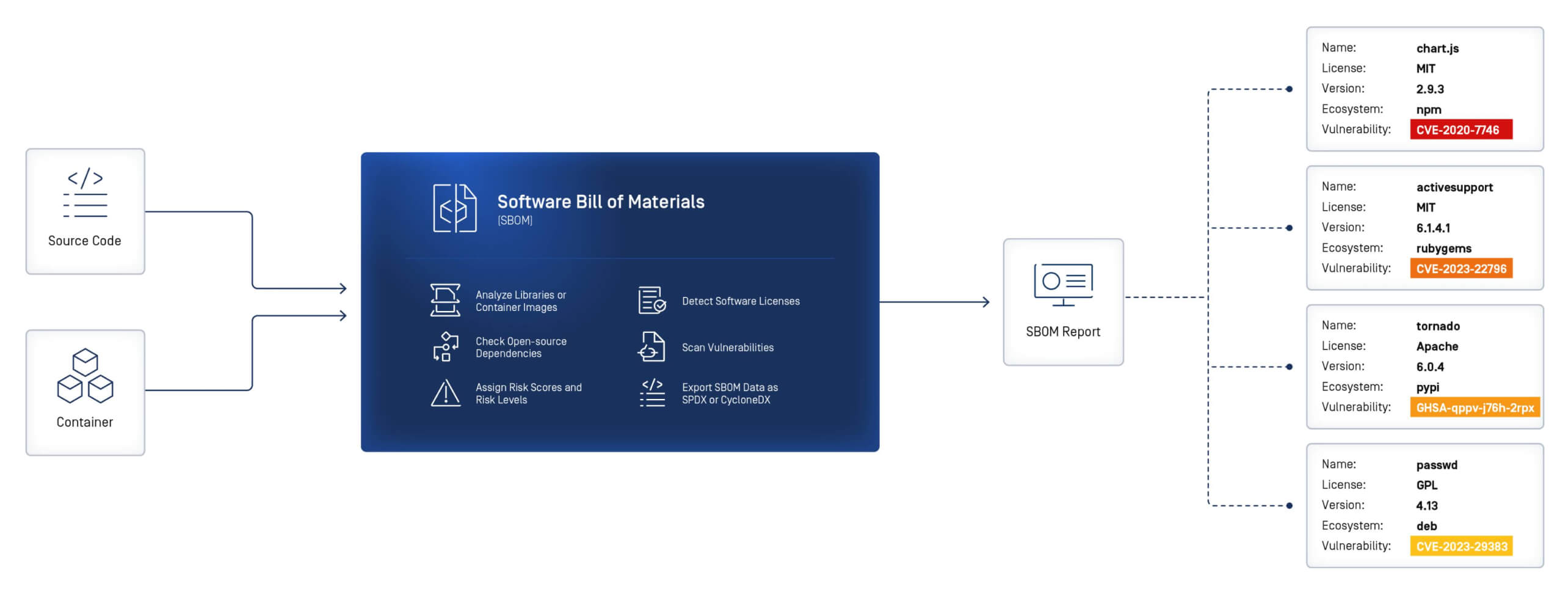
OPSWAT SBOM
OPSWAT SBOM oferă dezvoltatorilor un inventar precis al componentelor software din codul sursă și containere. Rămâneți înaintea atacatorilor, descoperiți amenințările și detectați vulnerabilitățile fără a afecta viteza de dezvoltare.
SBOM pentru pachete Software și artefacte
Permite echipelor de dezvoltare software să identifice, să prioritizeze și să abordeze vulnerabilitățile de securitate și problemele legate de licențiere ale dependențelor open-source.
SBOM pentru pachete Software și artefacte
Permite echipelor de dezvoltare software să identifice, să prioritizeze și să abordeze vulnerabilitățile de securitate și problemele legate de licențiere ale dependențelor open-source.
SBOM pentru imagini Container
Analizează imaginile containerului și generează SBOM pentru numele pachetului, informații despre versiune și vulnerabilități potențiale.
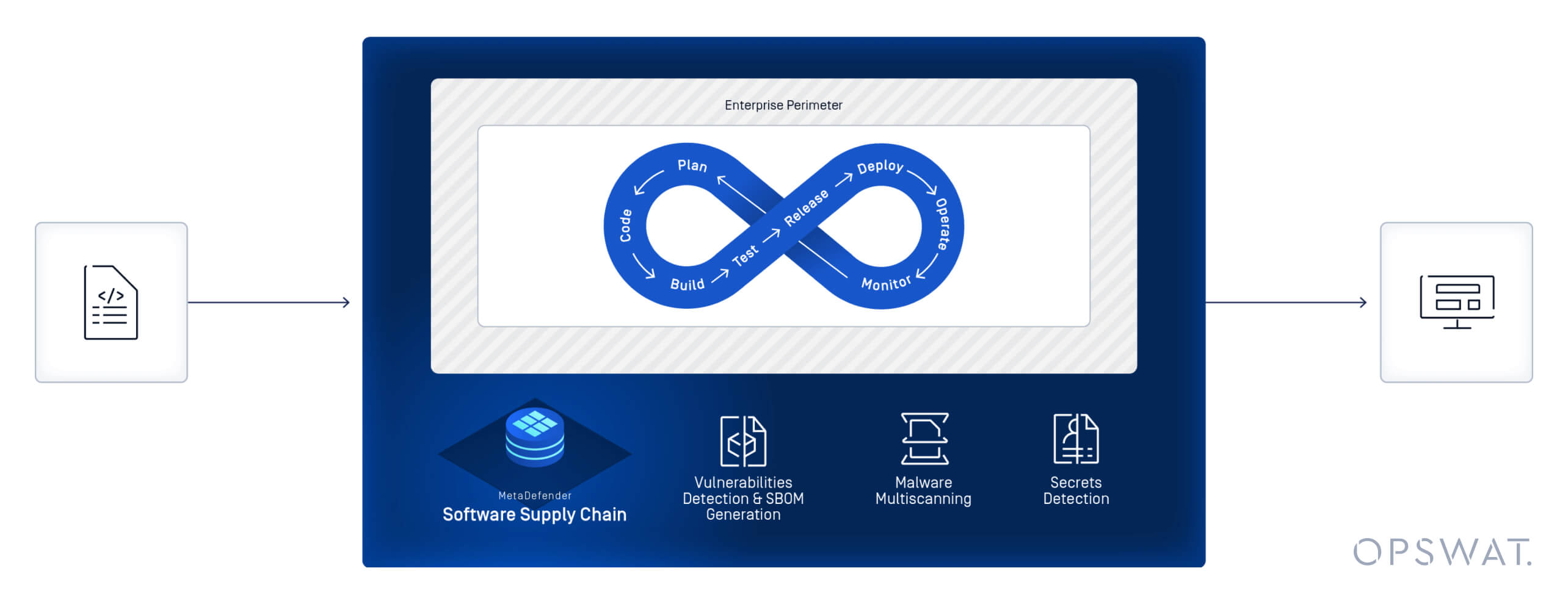
MetaDefender Software Supply Chain™
Mergeți dincolo de conformitatea SBOM și abordați atacurile avansate, în continuă evoluție, asupra lanțului de aprovizionare cu software.
OPSWAT MetaDefender Software Supply Chain oferă vizibilitate extinsă și o apărare solidă împotriva riscurilor din lanțul de aprovizionare. Cu ajutorul tehnologiilor noastre de detectare și prevenire a amenințărilor de încredere zero, ciclul de viață al dezvoltării software (SDLC) este protejat de malware și vulnerabilități, consolidând securitatea aplicațiilor și respectarea conformității.
Detectarea programelor malware în cod
Combinația de peste 30 de motoare antivirus crește ratele de detectare și împiedică în mod eficient infectarea stațiilor de lucru, a containerelor sau a codului sursă cu programe malware.
Identificarea secretelor greu codate
Proactive DLPTM identifică acreditările, cum ar fi parolele, secretele, token-urile, cheile API sau alte informații sensibile lăsate în codul sursă.
Secure containerelor împotriva atacurilor asupra Supply Chain
Evaluați și evaluați orice malware, vulnerabilități sau alte riscuri potențiale existente sub fiecare strat al unei imagini de container.
Integrare simplă
Indiferent dacă echipa dvs. utilizează depozite de cod sursă, registre de containere, servicii binare sau o combinație de instrumente, MetaDefender Software Supply Chain oferă integrări native cu platforme populare pentru a asigura securitatea pe tot parcursul SDLC.
Întrebări frecvente
Ce sancțiuni se aplică în cazul nerespectării orientărilor CERT-In SBOM?
Audituri de reglementare și potențiale restricții privind contractele cu guvernul și serviciile esențiale. Nerespectarea liniilor directoare CERT-In SBOM poate face organizațiile vulnerabile la încălcări ale securității datelor, ceea ce poate duce la amenzi mari.
Cât de des trebuie actualizate SBOM-urile?
La fiecare nouă versiune, actualizare, patch sau schimbare de furnizor.
Pot fi incluse componente open-source și terțe?
Da. Vizibilitatea completă a tuturor dependențelor - directe și transitive - este obligatorie.
Sunt scutite întreprinderile mai mici?
Întreprinderile nou-înființate din afara sectoarelor reglementate pot beneficia de un ajutor limitat, dar adoptarea este puternic încurajată.
Cum se aliniază CERT-In la standardele globale?
Abordarea Indiei reflectă cadre internaționale precum NIST și Legea UE privind reziliența cibernetică, asigurând compatibilitatea transfrontalieră.
Cum ar trebui tratată divulgarea vulnerabilităților?
Prin intermediul avizelor VEX și CSAF, integrate cu alertele CERT-In și sistemele interne SBOM.
Ce rol joacă automatizarea?
Automatizarea permite conformitatea continuă, reduce erorile umane și asigură scalabilitatea în mediile IT hibride.
Considerații specifice sectorului: Instituții financiare, Supply Chain și infrastructura critică
Sectorul financiar
Băncile și IFNB trebuie să alinieze practicile SBOM la mandatele de securitate cibernetică ale RBI, cu cerințe de audit mai stricte pentru gestionarea datelor sensibile.
Supply Chain
Furnizorii trebuie să livreze SBOM-uri ca parte a contractelor. Organizațiile trebuie să mențină inventare SBOM interne și externe pentru transparență și gestionarea riscurilor.
Infrastructura critică
Sectoare precum telecomunicațiile, apărarea și energia se confruntă cu suprapuneri de reglementare. Practicile SBOM trebuie să se integreze în cadrele mai largi pentru reziliența sistemelor și securitatea națională.
Ce urmează? Pregătirea pentru Cert-In SBOM Guidelines este esențială
Orientările CERT-In SBOM marchează un punct de cotitură pentru întreprinderile indiene. Ceea ce a început ca o concentrare restrânsă asupra SBOM-urilor s-a extins acum într-un cadru cuprinzător pentru vizibilitatea lanțului de aprovizionare cu software și gestionarea riscurilor.
Tehnologia OPSWAT SBOM merge dincolo de conformitate, încorporând vizibilitatea lanțului de aprovizionare în SDLC și integrând securitatea multistratificată cu depozitele de cod, registrele de containere și conductele DevOps.
Descoperiți cum OPSWAT vă poate ajuta întreprinderea să simplifice conformitatea CERT-In SBOM și să vă securizeze lanțul de aprovizionare cu software.



